We work directly with our clients' Information Security staff, leveraging their knowledge with our capabilities, to quickly complete sensitive IT security-focused projects under tight deadlines.
IT organizations can no longer manage their security on an ad-hoc, technology silo basis. An increasingly sophisticated threat landscape, tightening regulatory environments and the need for enterprise-wide SOA security services will no longer allow it. Whether PCI standards, HIPPA, Sarbanes-Oxley, tighter FFIEC oversight or your own internal auditors, IT management must not only implement an integrated "defense in depth" across tools, technologies, and people, but also demonstrate the efficacy and consistency of IT security processes.
Auditors and risk management firms dictate architectures and recommended processes. HHG helps our clients move from Power Point "slide-ware" to operational integrations that meet compliance and audit objectives while protecting the organization against increasingly complex threats.
Enterprise Security Goals
- Create an enterprise-wide, real-time Security View of the information from existing security tools, systems, network, applications and business management tools (integrating your existing tools, combined with real-time Business Service Views) to quickly correlate and identify potential realtime security threats.
- At the same time, insure that internal processes (like provisioning, identity & access management, secure development, sensitive data protection, infrastructure scanning, discovery and configuration management) can provide consistent and automated security services across your enterprise to secure your infrastructure from the individual data fields in messages, to data-at-rest, on up to your entire IT infrastructure, to prevent security breaches while enabling secure connections to your customers and partners as well as preventing the introduction of security threats from inside the organization.
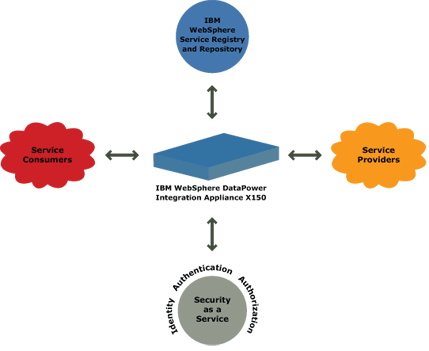
Products and integration points are still evolving, (especially in the use of federated registries or XACML for Fine Grain Authorization) and integration decisions that must be made today should also include an approach for fexibility tomorrow. Haddon Hill Group has been a leader in successful integration of policy-driven Security and dynamic SOA infrastructures.
The Security View eliminates noise and false positives by immediately correlating all of the enterprise's information sources to quickly identify true security incidents for automatic or Level One remediation, while reserving valuable security staff to quickly address potentially more serious threats. With proper design, the Security View also becomes the common foundation for warehousing, analytics, and investigations as well as reporting to managers, auditors and regulators.
This approach then creates compliance management and reporting common to multiple regulatory regimes to control cost and compliance risk. It replaces the costly ad hoc compliance approach that can actually create audit exceptions as well as ad hoc processes that can introduce security vulnerabilities into the IT infrastructure.
WS-Security Elements and Structure
A Basic SOAP Message with WS-Security
This common enterprise-wide set of security services, acting as the Policy Administration Point, can then enforce across the enterprise a common set of security policies stored in runtime registries, accessible to multiple federated Policy Decision Points and Policy Enforcement Points, including security appliances (such as the IBM DataPower XI50), Partner Gateways, ESBs, service containers, etc.
SOA Web Services Security as an internal set of Enterprise Security Services:
Service Oriented Architecture combined with standards-based Web Services have become the de facto integration standard for virtually all IT-intensive organizations. Using the standards-based integration technologies dramatically improves time-to-market, flexibility and TCO when deploying complex, highly distributed applications for both inter-enterprise as well as intra-enterprise integrations. These standards-based Web Services are built into all enterprise-class software products, including the use of the common WS security standards. Hence, every enterprise needs to implement a security infrastructure to provide these necessary Security services.
WS Security is based on XML policies and tokens where an integrated set of centralized policy-based security services serve as the enterprise's federated Policy Administration Points. At a minimum, the security service infrastructure needs to provide the capabilities of:
- Identity provider, Directory and administrator
- Security Policies specific to a user/service,
- Authentication, Authorization, and Fine Grained Authorization (FGAz)
- Logging, Certifications and Encryption
- Auditing and logging with analysis, including requests per unit of time, faults, denials of access, profiling of service consumers, etc.
HHG consultants have hands-on security project experience in:
- Automated security monitoring
- Automated compliance auditing
- Identity provisioning automation
- User role management
- Access request workflow automation
- AAA infrastructures and integration with various ESB products as Security Policy Enforcement Points
- PCI and HIPPA compliance
- Enterprise threat detection and remediation
- Sensitive data identification and security management
- Configuration management for security compliance
- Security View creation: integrating systems, network, applications and tools
- Identity and multi-factor access management
- Federated and distributed token processing including SAML and XACML
- Secure development lifecycle
- Security process implementation
- Application security monitoring and analysis
